CVE-2024-27288: 1Panel open source panel project has an unauthorized vulnerability.
First published: Wed Mar 06 2024(Updated: )
### Impact The steps are as follows: 1. Access https://IP:PORT/ in the browser, which prompts the user to access with a secure entry point. 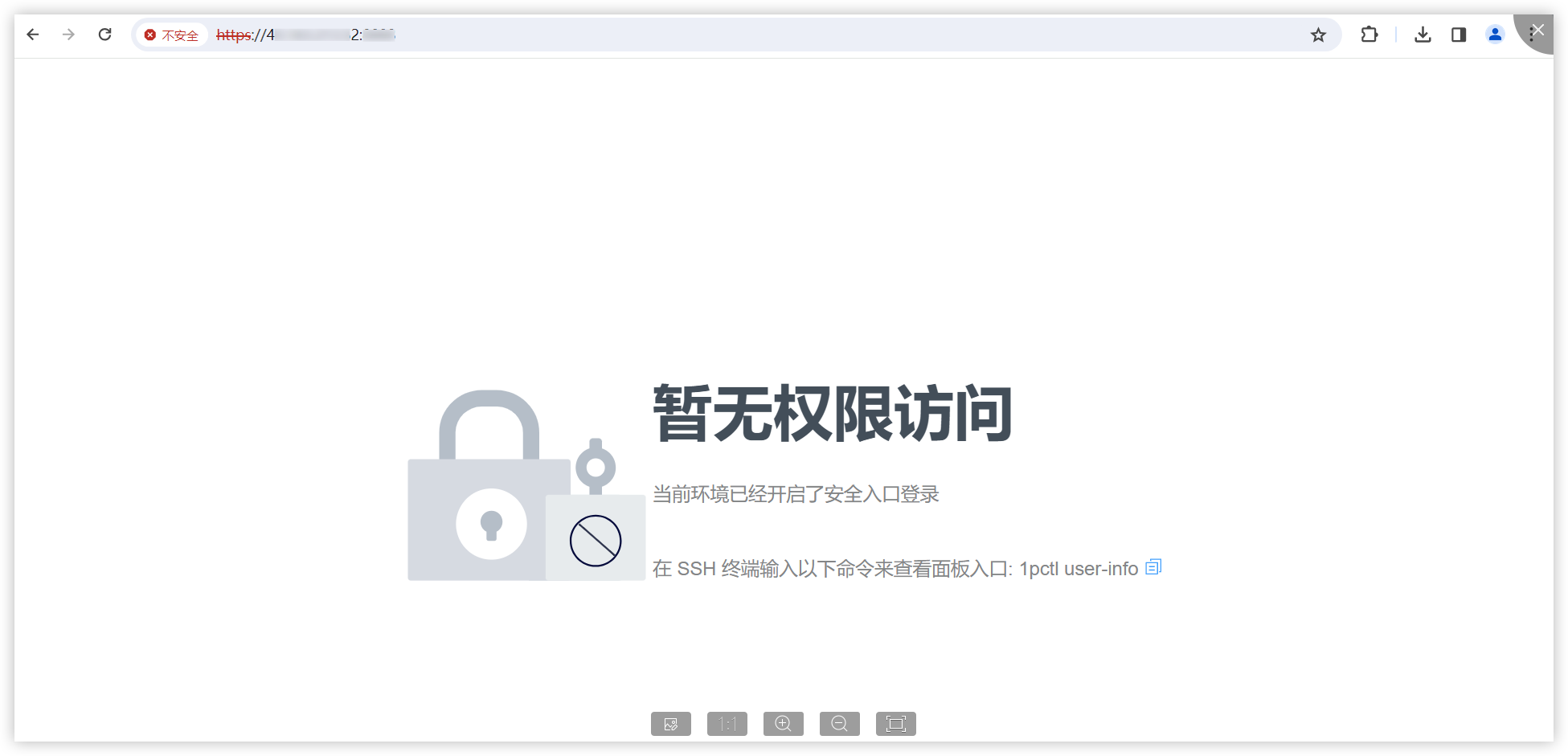 2. Use Burp to intercept: 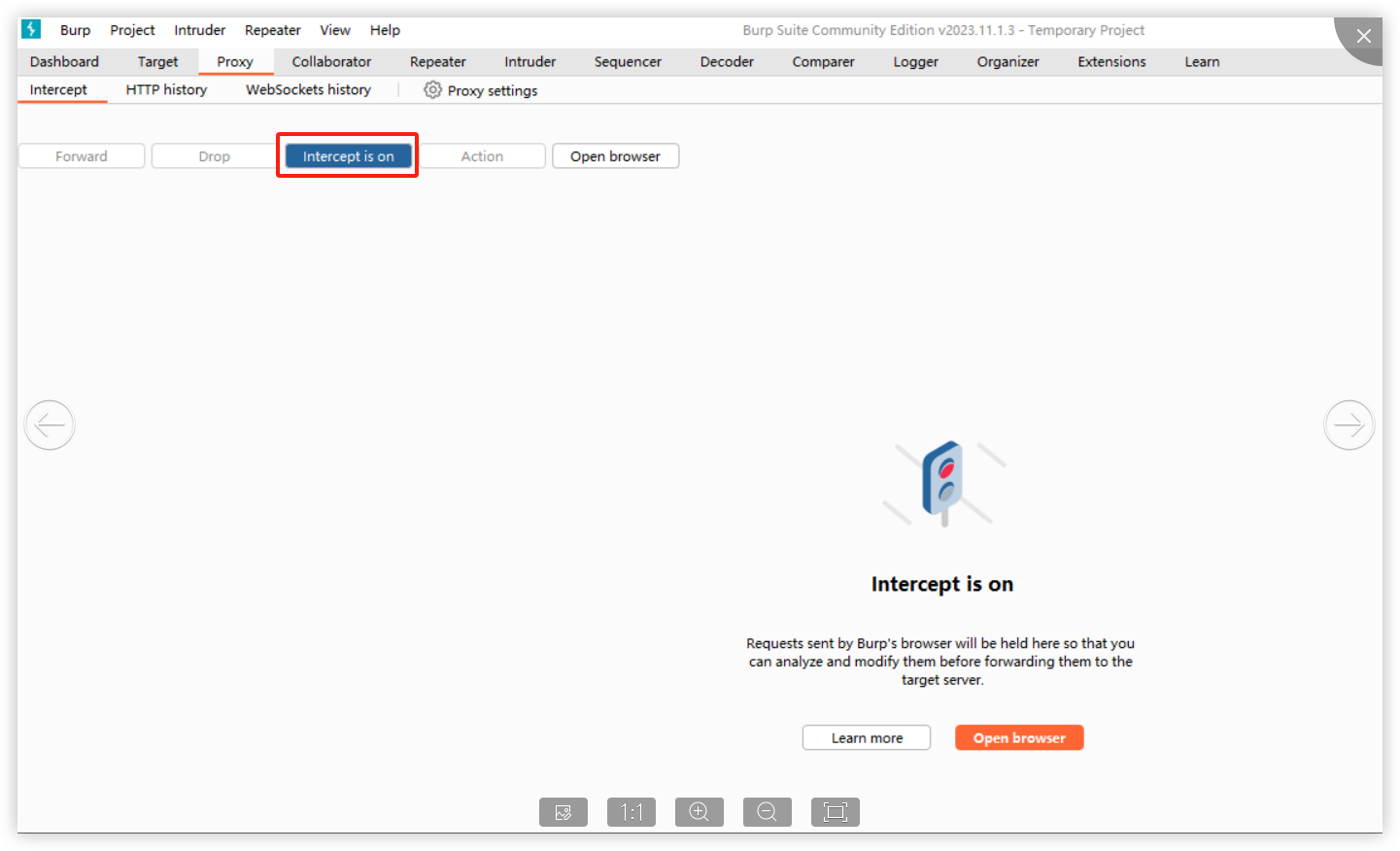 When opening the browser and entering the URL (allowing the first intercepted packet through Burp), the following is displayed: 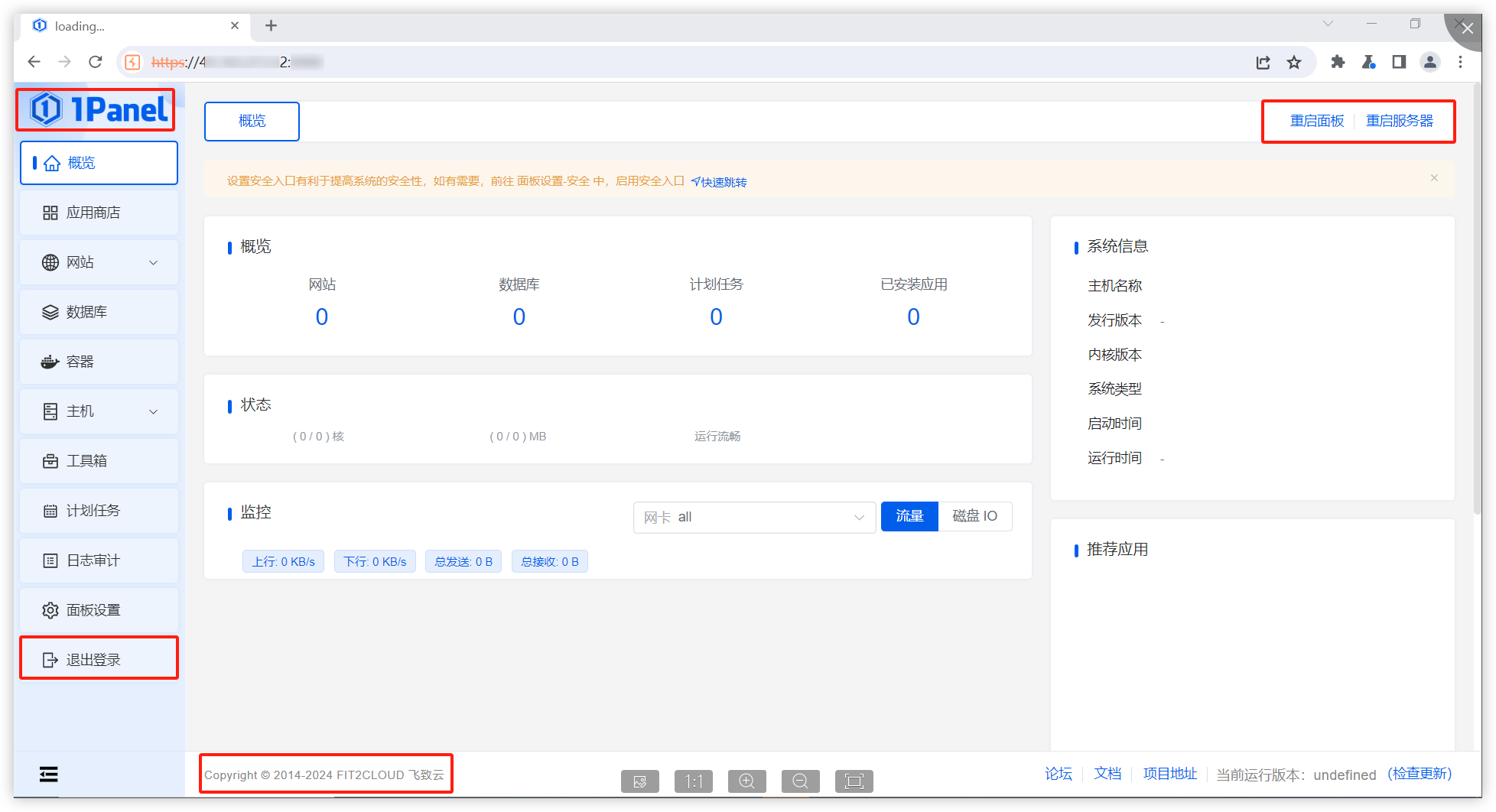 It is found that in this situation, we can access the console page (although no data is returned and no modification operations can be performed)." Affected versions: <= 1.10.0-lts ### Patches The vulnerability has been fixed in v1.10.1-lts. ### Workarounds It is recommended to upgrade the version to 1.10.1-lts. ### References If you have any questions or comments about this advisory: Open an issue in https://github.com/1Panel-dev/1Panel Email us at wanghe@fit2cloud.com
Credit: security-advisories@github.com security-advisories@github.com
| Affected Software | Affected Version | How to fix |
|---|---|---|
| go/github.com/1Panel-dev/1Panel | <=1.10.0-lts | 1.10.1-lts |
| 1Panel | <1.10.1-lts |
Never miss a vulnerability like this again
Sign up to SecAlerts for real-time vulnerability data matched to your software, aggregated from hundreds of sources.
Reference Links
Frequently Asked Questions
What is the severity of CVE-2024-27288?
The severity of CVE-2024-27288 is classified as high due to potential security risks associated with unauthorized access.
How do I fix CVE-2024-27288?
To remediate CVE-2024-27288, upgrade to version 1.10.1-lts or later of 1Panel.
Which versions of 1Panel are affected by CVE-2024-27288?
CVE-2024-27288 affects all versions of 1Panel up to and including 1.10.0-lts.
What kind of vulnerability is CVE-2024-27288?
CVE-2024-27288 is a web application vulnerability that could allow unauthorized access to sensitive information.
Is there a patch available for CVE-2024-27288?
Yes, a patch is available in 1Panel version 1.10.1-lts to address CVE-2024-27288.
- agent/first-publish-date
- agent/title
- agent/weakness
- agent/type
- agent/author
- agent/references
- collector/epss-latest
- source/FIRST
- agent/epss
- collector/mitre-cve
- source/MITRE
- agent/trending
- agent/source
- collector/github-advisory-latest
- source/GitHub
- alias/GHSA-26w3-q4j8-4xjp
- alias/CVE-2024-27288
- agent/software-canonical-lookup
- agent/last-modified-date
- agent/severity
- agent/event
- agent/softwarecombine
- agent/tags
- collector/github-advisory
- agent/description
- collector/nvd-cve
- source/NVD
- agent/software-canonical-lookup-request
- collector/nvd-api
- package-manager/go
- vendor/fit2cloud
- canonical/1panel
